Asset Profiling & Risk Assessment provides organizations with a strategic approach to managing their digital assets by offering in-depth profiling of each application or domain. This process involves collecting over 60 different data points, such as technology stack details, SSL certificate status, data collection, and operational dependencies. By thoroughly evaluating these factors, businesses can assess risk levels and allocate budgets more effectively - whether it's safeguarding mission-critical applications or addressing lower-priority platforms, this method ensures that resources are strategically distributed to identify and mitigate vulnerabilities. This comprehensive profiling and risk assessment process empowers organizations to make informed decisions about their security priorities, even without formal compliance requirements or existing security programs.
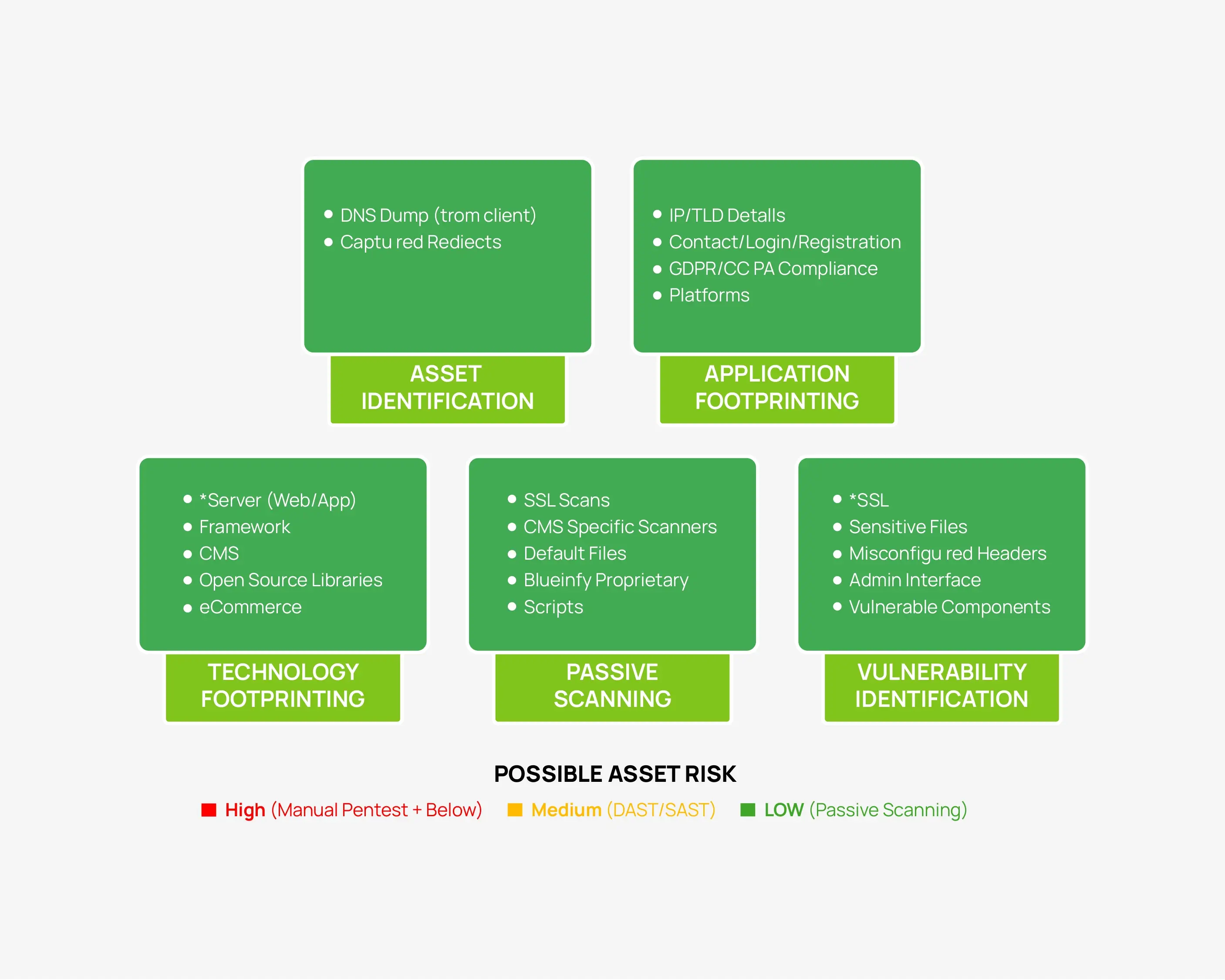
We developed a multi-phase approach to address the above challenges and help track assets, identify what type of security reviews should be performed for a particular risk of asset, and vulnerabilities, classify risk and provide the teams a list of items to work upon.
01
Asset Identification
- Identify whether website or domain is resolvable.
- Discover both internal network assets and internet-facing applications.
- Establish a complete map of digital assets, ensuring no critical areas are missed.
- Capture linked domains or subdomains (including those discovered via redirects).
- Lay the foundation for visibility into the organization’s entire application footprint.
02
Data Profiling
- Conduct detailed profiling of all identified assets using Blueinfy’s proprietary scripts.
- Gather critical information across 60 defined data points, covering:
- IP and TLD details
- Login/registration mechanisms
- Contact forms and communication channels
- GDPR compliance and cookie policy validation
- Profile across multiple platforms – web, mobile, and desktop.
- Obtain a comprehensive view of each asset’s infrastructure, components, and security posture.
- Enable targeted and efficient risk management and prioritization strategies.
03
Risk Classification
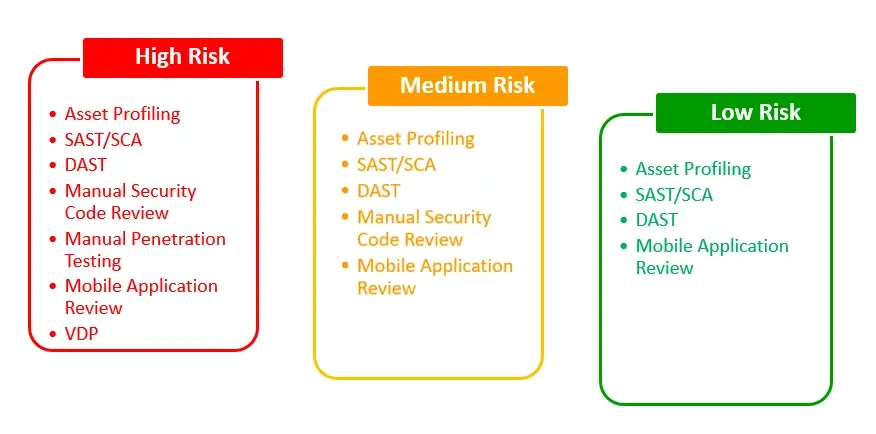
- Categorize domains based on technical risk and business criticality.
- Define evaluation and scoring criteria using collected data.
- Assign risk ratings (High, Medium, Low) to each asset.
- Use classification results to determine the appropriate type of security review required.
04
Data Classification / Passive Scanning (for Low-Risk Assets)
- Conduct passive, unauthenticated testing focused on identifying quick, low-severity vulnerabilities.
- Perform technology foot printing to gather insights on:
- Server details
- Frameworks and CMS (e.g., WordPress, Drupal)
- Application components and versions
- Utilize specialized tools for enhanced coverage:
- OpenSSL / testssl.sh for SSL configuration checks
- WPScan for WordPress
- Droopescan for Drupal
- Employ Blueinfy’s proprietary scripts for deeper, automated intelligence.
- Ensure non-intrusive testing that minimizes risk of detection or disruption.
05
Reporting, Remediation & Closure
- Generate comprehensive report to add discovered vulnerabilities in Vulnerability Management platform.
- Include details such as:
- Vulnerability descriptions
- Business and technical impact
- Recommended remediation steps
- Conduct recursive scans to verify fixes and identify new risks.
- Track open issues until verified closure, maintaining proactive defence against emerging threats.
06
Results & Metrics Dashboard
- Deliver a centralized dashboard for performance and exposure tracking.
- Present key metrics such as:
- Total number of assets/domains identified and risk-classified
- Type and count of testing efforts performed per domain
- Total vulnerabilities identified by each effort type
- Closure rate and remediation progress
- Trend analysis showing risk reduction over time (monthly/yearly)
- Provide leadership with data-driven insights into the organization’s evolving risk landscape.
07
Defence & Countermeasure Guidance
- Deliver practical defence strategies and countermeasure recommendations post-assessment.
- Guide developers with:
- Secure coding standards
- Security best practices
- Architectural hardening recommendations
- Ensure actionable, long-term improvements to the organization’s application and infrastructure security.